What Is the Salary of a CISO in the USA, UK, UAE, and Saudi Arabia?
The role of a Chief Information Security Officer (CISO) has become increasingly vital as organizations worldwide face escalating cyber threats and stringent regulatory requirements. This article provides an in-depth analysis of CISO salaries in the United States, United Kingdom, United Arab Emirates, and Saudi Arabia, exploring factors influencing compensation, regional variations, and future trends. 1.…
Read articleWhat Is the Price of the CEH Certification in the UK?
Introduction to CEH Certification The Certified Ethical Hacker (CEH) certification by EC-Council is globally recognized as a premier qualification for professionals in the field of ethical hacking and cybersecurity. It certifies the ability to identify vulnerabilities and protect systems against attacks using the tools and techniques hackers use—legally and ethically. If you’re based in the…
Read articleWhat Is the Price of the CEH Certification in Australia?
Introduction to CEH Certification The Certified Ethical Hacker (CEH) certification, developed by the EC-Council, is one of the most respected cybersecurity qualifications worldwide. It validates your skills in identifying vulnerabilities and securing systems using the same tools and methodologies that hackers use—legally and ethically. Whether you’re aiming for a career as a penetration tester, security…
Read articleCSRF (Cross-Site Request Forgery): How Hackers Hijack Sessions
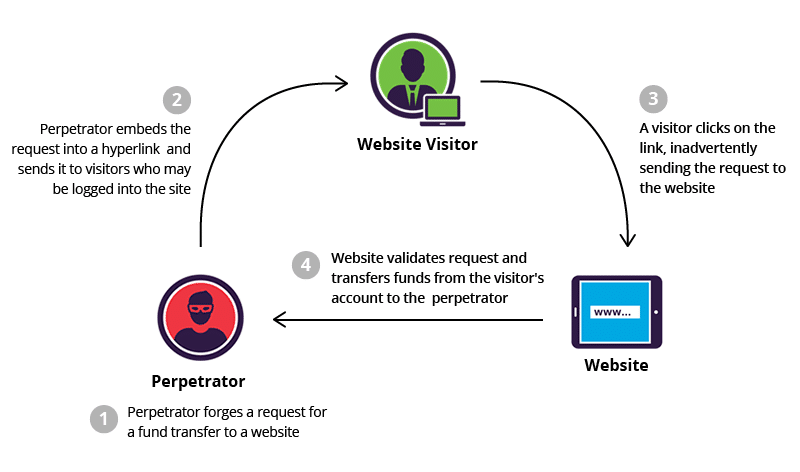
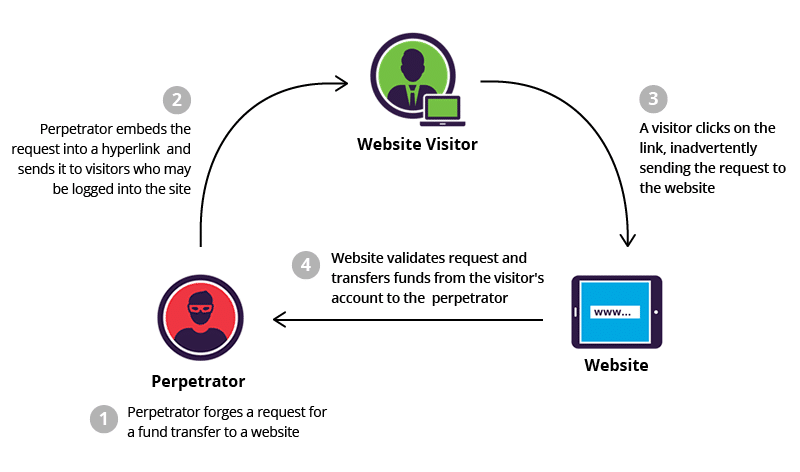
CSRF (Cross-Site Request Forgery): How Hackers Hijack Sessions CSRF (Cross-Site Request Forgery): How Hackers Hijack Sessions CSRF attacks, or Cross-Site Request Forgery, are stealthy web security vulnerabilities that enable hackers to perform session hijacking by tricking users into executing unwanted actions on trusted sites. This article explores the CSRF vulnerability, how attackers craft a CSRF…
Read articleCSRF (Cross-Site Request Forgery) : Comment les Hackers Détournent les Sessions
CSRF (Cross-Site Request Forgery) : Comment les Hackers Détournent les Sessions CSRF (Cross-Site Request Forgery) : Comment les Hackers Détournent les Sessions Les attaques CSRF, ou Cross-Site Request Forgery, sont des vulnérabilités de sécurité web discrètes qui permettent aux hackers de réaliser un détournement de session en incitant les utilisateurs à exécuter des actions non…
Read articleCross-Site Scripting (XSS) : Techniques d’Attaque et Défenses Selon WAHS
Cross-Site Scripting (XSS) : Techniques d’Attaque et Défenses Selon WAHS Cross-Site Scripting (XSS) : Techniques d’Attaque et Défenses Selon WAHS Les attaques XSS, ou Cross-Site Scripting, sont des vulnérabilités XSS critiques permettant aux attaquants d’injecter des charges utiles XSS malveillantes dans des applications web, compromettant ainsi la sécurité des applications web. Selon la certification WAHS,…
Read article