What Is the Price of the CEH Certification in Japan?
Introduction to CEH Certification The Certified Ethical Hacker (CEH) certification, offered by the EC-Council, is one of the most prestigious and internationally recognized credentials in the field of ethical hacking and cybersecurity. It certifies professionals who are equipped with the skills and tools to identify vulnerabilities in systems and secure them against malicious attacks—ethically and…
Read articleWhat Is the Salary of a Penetration Tester?
Introduction In today’s digital age, safeguarding information is paramount. Penetration testers, often known as ethical hackers, play a crucial role in identifying and addressing vulnerabilities within organizations’ systems. But what compensation do these cybersecurity professionals command across different regions? This article delves into the salaries of penetration testers, considering factors such as experience, location, and…
Read articleWhat Is the Validity Period of EC-Council Certifications?
Introduction In the cybersecurity world, certifications from leading organizations such as EC-Council carry significant weight. Titles like Certified Ethical Hacker (CEH), Certified Network Defender (CND), and Certified Penetration Testing Professional (CPENT) validate specialized knowledge and open the door to lucrative career paths. But how long are these certifications valid? Do they expire? How can professionals…
Read articleContrôle d’Accès Défaillant : Les Failles d’Autorisation Expliquées par WAHS
Contrôle d’Accès Défaillant : Les Failles d’Autorisation Expliquées par WAHS Contrôle d’Accès Défaillant : Les Failles d’Autorisation Expliquées par WAHS Le contrôle d’accès défaillant, répertorié sous OWASP A5, est une faille critique exposant des vulnérabilités d’autorisation qui permettent aux attaquants de contourner la sécurité pour accéder à des ressources non autorisées. Selon la certification WAHS,…
Read articleWhat Is the Best Cybersecurity Training in the UK?
Introduction In the face of escalating cyber threats and increasing digital reliance, the United Kingdom’s cybersecurity sector is experiencing a surge in demand for skilled professionals. Whether aiming for a role in ethical hacking, risk management, compliance, or information assurance, selecting the right training pathway is critical to building a successful career in this dynamic…
Read articleSSRF Unmasked: How Hackers Exploit Server-Side Request Forgery
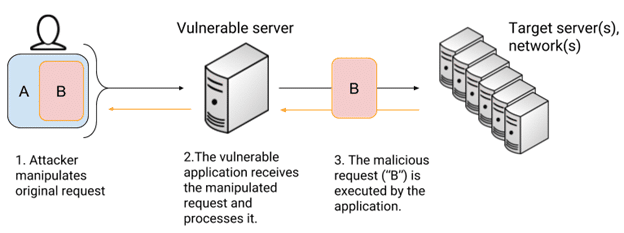
SSRF Unmasked: How Hackers Exploit Server-Side Request Forgery SSRF Unmasked: How Hackers Exploit Server-Side Request Forgery SSRF attacks, or Server-Side Request Forgery, are stealthy SSRF vulnerabilities that trick servers into making unintended requests, often exposing internal systems. This article unmasks how hackers leverage SSRF payloads to target cloud SSRF environments like AWS SSRF, Azure SSRF,…
Read article