SSRF Démasqué : Comment les Hackers Exploitent le Server-Side Request Forgery
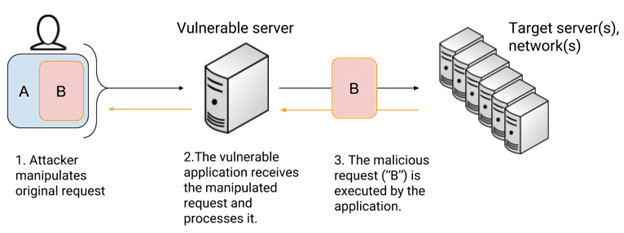
SSRF Démasqué : Comment les Hackers Exploitent le Server-Side Request Forgery Les attaques SSRF, ou Server-Side Request Forgery, sont des vulnérabilités SSRF furtives qui incitent les serveurs à effectuer des requêtes non intentionnelles, exposant souvent des systèmes internes. Cet article dévoile comment les hackers exploitent des charges utiles SSRF pour cibler des environnements SSRF dans…
Read articleWhere to Take the CEH Certification?
Introduction to the CEH Certification The Certified Ethical Hacker (CEH) certification, issued by the EC-Council, is a globally recognized credential for professionals in the field of cybersecurity. It validates your ability to identify, exploit, and secure information systems using the same knowledge and techniques as malicious hackers—but with legal and ethical intent. The CEH is…
Read articleWhat Is the Price of the CEH Certification in China?
Introduction to CEH Certification The Certified Ethical Hacker (CEH) certification, developed by the EC-Council, is a globally respected credential that validates a cybersecurity professional’s ability to think and act like a hacker—but in a lawful and ethical way. CEH-certified professionals use the same tools and techniques as malicious hackers to assess system vulnerabilities and help…
Read articleInjection SQL : Comprendre et Exploiter cette Vulnérabilité Critique
Injection SQL : Comprendre et Exploiter cette Vulnérabilité Critique Injection SQL : Comprendre et Exploiter cette Vulnérabilité Critique L’injection SQL, ou SQLi, est une vulnérabilité SQLi majeure permettant aux attaquants d’insérer du code SQL malveillant dans les champs d’entrée d’une application web, compromettant ainsi la sécurité des bases de données. Ce tutoriel sur l’injection SQL…
Read articleSQL Injection: Understanding and Exploiting This Critical Vulnerability
SQL Injection: Understanding and Exploiting This Critical Vulnerability SQL Injection: Understanding and Exploiting This Critical Vulnerability SQL injection, or SQLi, is a major SQLi vulnerability that allows attackers to inject malicious SQL code into web application input fields, compromising database security vulnerabilities. This SQL injection tutorial explores how it works, its SQL injection exploitation methods,…
Read articleCSRF (Cross-Site Request Forgery): How Hackers Hijack Sessions
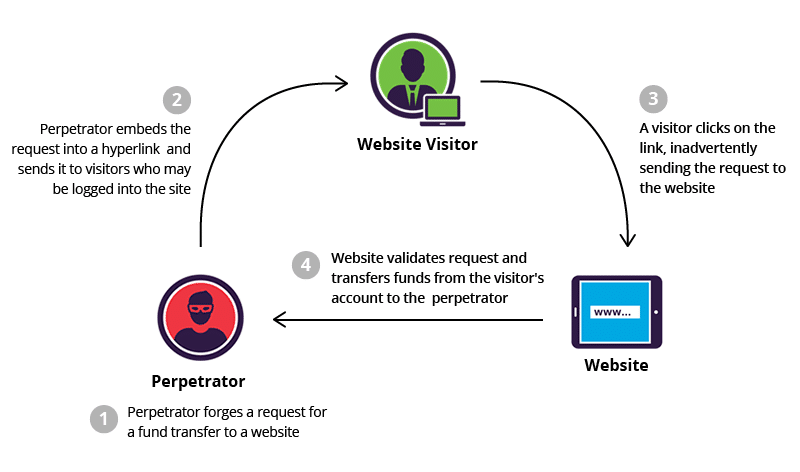
CSRF (Cross-Site Request Forgery): How Hackers Hijack Sessions CSRF (Cross-Site Request Forgery): How Hackers Hijack Sessions CSRF attacks, or Cross-Site Request Forgery, are stealthy web security vulnerabilities that enable hackers to perform session hijacking by tricking users into executing unwanted actions on trusted sites. This article explores the CSRF vulnerability, how attackers craft a CSRF…
Read article